
This article relates to episode 5 in the series ‘Cyber Security in the Ancient World’.
The 4th-century BCE Greek military author Aeneas Tacticus was one of the earliest Greek writers on the art of war and is credited as the first author to provide a complete guide to securing military communications. According to Aelianus Tacticus and Polybius, he wrote a number of other treatises on the subject as well. And Polybius also described Aeneas’ design for a hydraulic semaphore system.
Little is known about the life (and therefore of the direct military, cryptographic or steganographic experiences) of Aeneas Tacticus. Aeneas Tacticus, or Aineias the Tactician wrote a treatise on tactics known as How to Survive Under Siege or On the Defence of Fortified Positionsaround 360-355 BCE.[1] A date around 360-355 BCE makes Aeneas Tacticus’ work not only the oldest known military manual in history but also the oldest known work on cryptography and steganography.[2]Chapter 31 of the work is specifically dedicated to recommendations regarding the use of cryptographic and steganographic devices and methods during sieges.[3] In the course of chapter 31 the author discussed twenty-one different methods for secret communication, offering us a detailed catalogue of methods for ancient communication security. Next to this, we know from Polybius that in a now lost work Aeneas also discussed the use of fire signalling for secret communication (Polybius, Histories, 10.44-46).[3]
The focus in How to Survive Under Siege is upon hiding messages to smuggle them in and out of the besieged polis and not upon encoding them to prevent their being read and understood by hostile agents (either within or without the city walls). Indeed, this is a recurring theme throughout Aeneas Tacticus’ whole work, in which he made clear that establishing secure and mutually comprehensible means of secret communication were of vital importance. The polis’ inhabitants had to secure all forms of communication that went in and out of the city (Aeneas Tacticus, How to Survive Under Siege, 4.1-4; 5.1; 9.2; 10.6; 10.11; 10.18-19; 10.25-26; 11.3-6; 12; 18.3-6; 18.8-11 (see also Polyaenus, Stratagems of War, 2.36); 18.13-21; 20; 22.5; 22.7; 23.7-11; 29.3-10).[4] Given the significant risk of citizens within the polis conspiring and communicating with the enemy, it was vital for the commanding forces to be able to communicate between themselves secretly and securely in Aeneas Tacticus’ view. All methods for secret communication that Aeneas Tacticus discussed in chapter 31 of the work are related to this theme of internal treachery, and to his idea of an enemy who is always nearby.
A careful cataloguing of the several types of secret communication that Aeneas Tacticus discusses in his treatise indicates that he was most familiar with simple steganographic devices for secret communication – and preferred these over encrypted messaging for siege contexts.
In chapter 31.14 of How to Survive Under Siege Aeneas Tacticus discusses a straightforward strategy of secret communication involving the concealment of writing under the wax of a wax-tablet. According to Aeneas Tacticus, a non-encrypted secret message would be written on the base of a tablet and then wax was poured over it, and a second – open message would be written on the top film of wax. When this tablet was delivered, the recipient – who knew or anticipated that a message was written under the wax – would scrape off the wax to read the message hidden underneath and send any reply in the same way (31.14).
This example is clearly based upon the story of Demaratus’ message to the Spartans derived from Herodotus’ Histories (7.239; see also Aulus Gellius, Attic Nights, 17.9.6; Julius Africanus, Kestoi, 53; Justin, Epitome of the Philippic History of Pompeius Trogus, 2.10.13; Polyaenus, Stratagems of War, 2.20).[5] However, Aeneas Tacticus did not simply follow Herodotus’ earlier account verbatim. After discussing how the person in his example (probably Demaratus) sent a secret message to the Spartans following the details of his Herodotean source closely, Aeneas Tacticus suggests that a message was sent back in the same way (31.14) – as if this were a useful practical way of secret communication that had taken place between two parties. He then adds two other possibilities, as if to show that he could improve on his sources by supplementing them with ideas of his own. First, we see the possibility to write a message on the base of a boxwood tablet, and then whitewash the tablet and paint a picture over it to render the writing invisible. To make the writing visible again a recipient had to place the tablet in water to dissolve the paint (31.14-15). Aeneas Tacticus’ second alternative suggestion is to use a hero’s plaque (an image of a hero usually left in a shrine) for the same purpose (31.15-16).[6]
Clearly, Aeneas Tacticus considered that his alternatives would have worked more effectively as practical steganographic devices than the original method described by Herodotus. It is plausible that Aeneas Tacticus (quite sensibly) believed that a seemingly empty tablet in transit would have attracted too much suspicion if it fell into the wrong hands. Aeneas Tacticus based another example of secret steganographic communication on Herodotus.
In 31.28-29 Aeneas Tacticus discussed the Herodotean story of Histiaeus’ message to Aristagoras tattooed on a slave’s head (31.28-29). This example from Herodotus again fits in well with the broader theme of Aeneas Tacticus’ work on sieges, since here we are dealing once again with a hidden message being smuggled out of a besieged city (Herodotus, Histories, 5.35.2-4; see also Aulus Gellius, Attic Nights, 17.9.18-27; Polyaenus, Stratagems of War, 1.24). Indeed, this case is included as an example of the importance of the use of trustworthy messengers for secret communications during a siege, which is a recurring theme in Aeneas Tacticus’ work (Aeneas Tacticus, How to Survive Under Siege, 9.2; 10.6; 10.11; 10.25-26; 22.5; 22.7; 31). Unlike his reworking of the Demaratus’ story reported by Herodotus, however, here Aeneas Tacticus includes the names (Histiaeus; Aristagoras) and places (Miletus) that Herodotus had supplied in his version, thereby lending credibility and authority to his own account.
Aeneas Tacticus discusses seven further examples of steganographic messages that could be sent hidden in or under clothing, footwear, armour, jewellery, and even a dog collar. Four examples are based on Aeneas Tacticus’ sources (31.6; 31.23; 31.25-27; 31.31-32), while three examples were his own suggestions (31.4-5; 31.7; 31.9; 31.9). Amongst his simple suggestions are to hide a message under a breastplate (31.8), to sew one into a bridle-rein (31.9-9b), or to hide it in between layers of clothing (31.23; see also Julius Africanus, Kestoi, 53; Philo of Byzantium, Compendium of Mechanics, D.78 (102.37–39) in: Thévenot, Boivin, et al., 1693, Veterum Mathematicorum Opera, 102).[7]
Aeneas Tacticus also discusses how a message was once sent bound to a wound on a man’s leg (31.6), and how in Epirus and Thessaly it was the custom to take a dog away from his home, hide a secret message in its collar, and then send it back home (31.31-32).[8]A slightly more complicated method compared to these is found in 31.7, where Aeneas Tacticus suggests to write messages on pieces of lead that could be rolled up and worn as women’s earrings.[9] Significantly, the lead could be rolled up, making it possible to send a closed and sealed message hidden in plain sight. This makes the method a noticeably clear example of Aeneas Tacticus’ interest in hiding messages rather than encrypting them.
Another slightly more complicated method can be found in 31.4-5. Here Aeneas Tacticus discusses the sending of secret messages by using a messenger without the messenger knowing about this. Before sending out the messenger the sender had to insert a secret letter into the messenger’s sandals.[10]He would then send the messenger to the recipient with a non-secret letter to provide a cover for his actual mission. The recipient could reply in the same way if requested (31.4-5; see also Julius Africanus, Kestoi, 51; Philo of Byzantium, Compendium of Mechanics, D. 81 (102. 45-50) in: Thévenot, Boivin, et al. 1693, Veterum Mathematicorum Opera, 102.).[11] These seven examples show Aeneas Tacticus’ interest in steganographic messages that were hidden in simple ways almost in plain sight, by using commonly known household objects
In chapter 31.10-13 Aeneas Tacticus discusses some no less simplistic though rather more laborious way of sending secret messages by using an oil-flask and a bladder. According to Aeneas Tacticus, one could inflate a bladder and write on it with ink mixed with glue. Once the writing was dry one had to deflate the bladder, press it into a flask, and inflate it again. Hereby, the glue would stick the bladder to the insides of the flask. Then one had to fill the flask (or technically the bladder lining it) with oil. In this way, the bladder would have become (nearly) invisible. Upon receiving the flask, the recipient had to pour out the oil, re-inflate the bladder and read the text.[12] He could then wipe off the text with a sponge and reply in the same way (31.10-13). This particular method of steganographic communication is not only laborious but demands access to a panoply of domestic supplies. Indeed, such a method for securing the secret communication of hidden (though not encoded) messages would have been highly impractical on a battlefield since both parties would have needed flask, bladders, ink, glue, and oil, et cetera. However laborious, the method might have been useful as a means of securing a secret communication in a siege defence, and therefore offers us a salient reminder that this is the specific context of Aeneas Tacticus’ work.
Aeneas Tacticus’ predominant focus in his treatise on How to Survive Under Siege is upon providing his readers with a catalogue of devices and stratagems suitable for secret communication under siege conditions. His priorities are upon smuggling concealed messages in and out of the polisor city – and he focuses upon concealment rather than encryption as the priority in securing these communications. In fact, so confident is Aeneas in the security of these various steganographic devices that he has comparatively little to say about the risks of these messages being intercepted and read by hostile agents. In fact, there are only two examples in How to Survive Under Siege in which Aeneas Tacticus appears to take seriously such a risk and to mitigate against it by sending a hidden (steganographic) message that is also for extra security encrypted or encoded (a cryptographic message) in some way (31.1-3).
Aeneas Tacticus’ only two suggestions for the use of cryptography can be found in passage 31.30-31. In this passage Aeneas Tacticus suggests that, instead of marking a slave’s head with easily recognisable words or letters, one could instead write by replacing vowels with dots (31.30-31), or any other letter or symbol (31.31).[13] The encoded messages created here by using this very basic form of encryption through partial substitution would help to add an additional layer of security should the messenger-slave be intercepted by hostile agents and his head shaved to reveal the message on his scalp. [14] Aeneas Tacticus’ methodology here represents the first known substitution cipher recommended for use in warfare. Yet, it is important not to overlook the fact that it is presented by Aeneas Tacticus as a secondary device, an insurance policy of sorts, to support his primary stratagem recommending a steganographic approach as the foundation to successful secret communication.
The only two examples of methods that involves a combination of cryptography and steganography can be found at the start of chapter 31 of How to Survive Under Siege. In passage 31.1-2 Aeneas Tacticus discusses how a message could be written by marking letters in a book or document with dots and the book or document with the message then hidden in baggage. The recipient had to make a transcript of all the marked letters to understand the message (31.1-2). As an alternative, Aeneas Tacticus suggests that instead of using a book or document as the vehicle for the message, one could simply write a letter and then add the markings (31.3) – which obviously had to be as inconspicuous as possible by placing them far apart and making them as small as possible (31.1-3).
Clearly marked letters in a text would have attracted suspicion especially for trained people who would have been trying to uncover their enemy’s secrets, and especially if there were a pattern in the text with e.g., every third letter being marked. One, therefore, had to avoid clear marking and patterns when using this technique. The combination of cryptographic and steganographic encryption here, as in the previous case, makes the method more secure. However, Aeneas Tacticus is clearly less confident in the protection offered by encryption than he is in the protection offered by concealment. Although he has recommended numerous steganographic techniques that work (so he suggests) on their own, here he once again recommends that the coded message or text is also hidden and concealed in a bag to secure its transmission. His personal preference for secure secret messaging falls clearly to the side of steganography rather than cryptography.
A possible explanation for Aeneas Tacticus’ comparative lack of confidence in cryptographic devices, may be traced to his account in his treatise of the use of astragali (also known as knucklebones or talus bones) to send secret messages (31.16-22).[15] As becomes clear from Aeneas Tacticus’ description, one could pierce 24 holes into an astragalus to represent the 24 letters of the Greek alphabet. Only knucklebones of hooved animals – like sheep or goats – were useful for this purpose since these are almost square or rectangular and, therefore, have four more or less flat sides, on to which the 24-letter Greek alphabet naturally fell in to four neat groups of six letters.[16]
Whenever someone wanted to communicate a message by using an astragalus, this person had to draw a thread through its holes. In other words, he would ‘sew’ a message through an astragalus, and this transposing of letters would compose a simple transposition cipher (31.16-19).[17] The unthreading obviously took place in the reverse order, since the decoding necessarily started by unthreading at the end. Consequently, all the letters of the message appeared in reverse order. Therefore, to understand the intended message properly, the recipient had to turn the letters back into their normal order. Because of its size, a message sent using an astragalus could not have been much longer than one or two words or a very short sentence. The message ‘Enemy Attacks At Dawn’ could, for example, have been abbreviated to EAAD. Yet, the use of such a small object must have made the use of astragalifor this form of secret communication very time consuming and very difficult in practice. One would easily end up with a ball of thread whereby it was no longer possible to find the correct holes – making the use of astragalirather troublesome for the sender, and even more so for the receiver, as Whitehead, and Hunter and Handford point out.[18] Therefore, it is questionable whether the method may have functioned well.
It seems plausible that Aeneas Tacticus found out for himself that using the astragali for secret communication was laborious, since he described the method not only as the most secret, but also the most difficult (or ‘troublesome’ as Whitehead translates it; 31.16).[19] Since the method was rather complicated and very time consuming, Aeneas Tacticus accordingly suggests two simpler variations. Instead of an astragalus one could either use a rectangular piece of wood (31.20) or a wooden disk (31.21-22) in which one would then pierce 24 holes as in the bone astragalus. When using the disk, one had to prick holes in the centre of the disk too. Whenever a letter occurred twice in a row, one had to pull the thread through one of the holes in the centre in between the two other letters (31.22).
Figure 1 shows two possible reconstructions show what this disk might have looked like. Diels’ suggestion( Figure 1; left) in which the letters alpha to omega are written clockwise in their normal order at the edge of the disk. Diels incorrectly describes this as a reconstruction of an astragalus while it clearly represents Aeneas Tacticus’ wooden disk.[20] Figure 1 (right) shows Welskopf’s reconstruction in which the first four letters – alpha, beta, gamma, and delta – can be found at the top, bottom, and left and right side of the disk as on a compass where north, south, east, and west are pointed out. The rest of the letters can be found right opposite each other on the disk starting at the top with a letter of the right side, then a letter on the left side and so on.[21] Yet, it is more plausible that the letters were ‘written’ in alphabetical order to avoid making this already complex method yet more complex again.
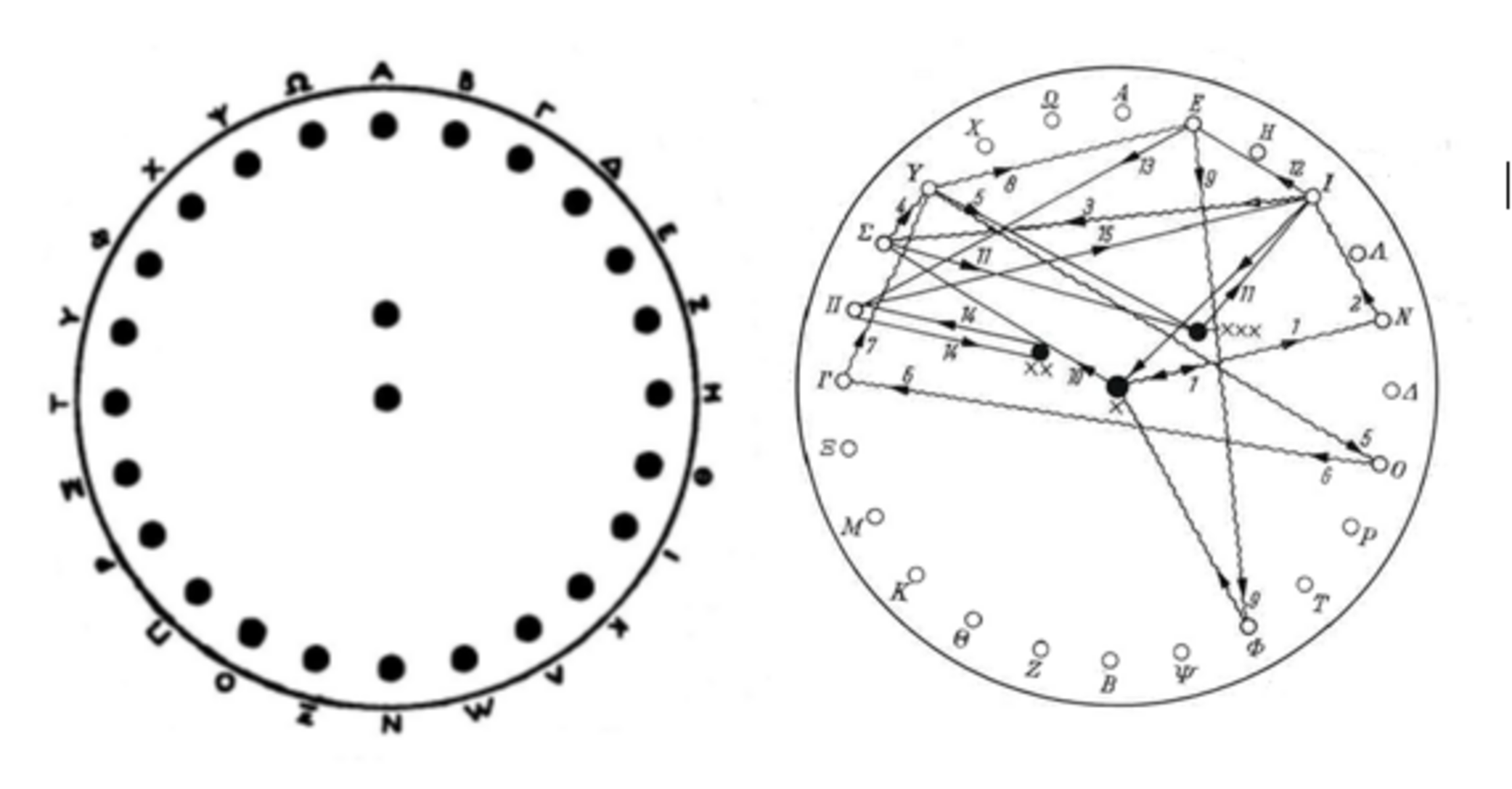
Aeneas mentions that the extra holes in the middle were added to prevent suspicion from being raised (31.21) – though what exactly he meant by this is unclear. Translations and commentaries seem to have overlooked this point. It might be that there is an omission in the text here, but another intriguing possibility is that one could have pulled a thread through the holes in the middle in order to wear the disk as a necklace – in the same way as the lead earrings described as a steganographic device in the treatise were designed to be worn as jewellery (31.7). Indeed, this interpretation fits in well with Aeneas Tacticus’ wider approach to such devices and stratagems in How to Survive Under Siege.
To conclude, some of the methods Aeneas describes are simple, like hiding a letter under clothing or in a bag. Others are more complicated, culminating in the use of the astragali. We cannot know how many of these methods were used in warfare. Yet, the methods Aeneas described must have been useful during sieges - at least theoretically.
[1] Aeneas Tacticus is often identified as Aineias of Stymphalos, an Arcadian general from the 4th century BCE who is mentioned in Xenophon’s Hellenica (Xenophon, Hellenica, 7.3.1); Barends 1955; 171; Bliese 1994, 108; Brownson 1918, 281; Chaniotis 2013, 441; Dain & Bon 1967, vii; xii; David 1986, 343; Delebecque, 1957, 430; Hug 1877, 28 ff.; Hunter & Handford, 1927 ix-x.; xxii; xxiv-xxv; 264; Millett 2013, 65; Oldfather 1923 7; Rawlings 2007, 13; Starr 1957; 68; Vela Tejada 2004, 141-142; Usher 1970, 210-211; Whitehead 1990, 10-12; Winterling 1991, 196. See also Vela Tejada 1991. It is likely that Aeneas wrote at least four other works on military strategy that have been lost. Three of the works are referred to in How to Survive Under Siege: a work on military preparations (7.4; 8.5; 21.1; 40.8); a work on procurement (14.2); and a work on encampment (21.2). Scholars presume that Aeneas also wrote a work on conducting siege operations (Aelian, The Tactics, 1.2; 3.4; Julius Africanus, Kestoi, 37; Bliese 1994, 108; Hanson 2007, 3; Hunter & Handford 1927, xii-xiii; Oldfather 1923, 4; 8-9; Vela Tejada 2004, 142-143; Rawlings 2007, 139; Whitehead 1990, 14-15; see also Vela Tejada 1991).
[2]Chaniotis 2013, 446; Jenkins 1999, 35; Moore 2013, 462; Vela Tejada 2004, 141-142. See also Vela Tejada 1991.
[3] Kelly 1985, 141-169; Sheldon 1987, 45; West 1988, 42; Whitehead 1990, 184.
[4] Burliga 2008; Pretzler 2018; Liddel 2018, 123; Rawlings 2007, 139; Spence 2010, 26; Shipley 2018; Whitehead 1990, 4; 20-24; Williams 1904, 390.
[5] See for a parallel from Roman times: Herodian, History of the Empire from the Death of Marcus, 7.6.5. When using a source Aeneas Tacticus did not literally quote it. Instead, he paraphrased his sources to bring out his own points in the clearest way, thereby omitting unessential details and sometimes adding information to the original (Brown 1981, 388; Burliga 2008; Pretzler 2018; Shipley 2018).
[6] In this second example another type of paint would be used since Aeneas Tacticus recommends that oil was needed to dissolve the painting instead of water (31.16).
[7] See for a Roman parallel: Ammianus Marcellinus, Roman History, 18.6.17-19; Frontinus, Stratagems, 3.13.3-6; Florus, Epitome of Roman History, 1.40.15-16; Orosius, Seven Books of History Against the Pagans, 6.2.14.
[8] See for a parallel from Roman times: Frontinus, Stratagems, 3.13.5-8; Pliny, Natural History, 10.53 (37). A link can be made to the use of animals as secret messengers in the 20th century. For the role of carrier pigeons in the Second World War, see e.g.: O’Connor 2018.
[9] See for a parallel from Roman times: Cassius Dio, Roman History, 46.36; Frontinus, Stratagems, 3.13.7.
[10] To make sure that the hidden message was not affected by water and mud, Aeneas Tacticus suggested that it be written on a piece of lead (31.4). Whitehead incorrectly presumes that Ovid suggested this same method in Ars Amatoria, 3.624 (Whitehead 1990, 184). However, Ovid simply mentioned that one could hide a letter between a foot and a sandal amongst a selection of simple methods to communicate in secret quickly and easily (Art of Love 3.619-630).
[11] This method could have been useful if one did not trust his messenger.
[12] This is not an example of the use of invisible ink since the recipient simply had to pour out the oil to be able to read the text again. He did not have to use e.g., charcoal to make the text visible again. For the use of invisible ink in antiquity see Ausonius, Epistles, 28.21-22; Ovid, Ars Amatoria, 3.627-630; Philo, Compendium of Mechanics, D. 77 (102.31-36); Pliny the Elder, Natural History (26.39 (62)).
[13] Bauer – based on Hunt 1929 – suggests that the ancient Greeks were familiar with the cryptographic principle of replacing letters by other letters (Bauer 2017, 96). See also Plutarch, Dion; Timonides, Fragment 1, in: Brill’s New Jacoby (561)); Timaeus, Fragment 114; in: Brill’s New Jacoby (566). When discussing this passage, scholars – starting with Von Gutschmid in 1880 – have typically only focused upon attempting to link this example to a historical event: the war between Dionysius II of Syracuse, and his opponents Dion and Heracleides in 357 BCE. These scholars seem to have overlooked the fact that this short passage provides the only two suggestions of cryptographic methods out of the total sum of twenty-one methods for secret communication that Aeneas Tacticus discussed in chapter 31 of his work – again clearly showing that Aeneas Tacticus was far more interested in steganographic (hidden) messages than in cryptographic (coded) messages (Bengtson 1962, 460; Glotz & Cohen 1936, 410-411; Dain & Bon 1967, 75; Oldfather 1923, 5-7; Von Gutschmid 1880, 588-590; Whitehead 1990, 191).
[14] From around 600-500 years BCE Hebrew scholars were already using a substitution system known as the Atbash cipher and Aeneas Tacticus may have based his simple cipher on this model. See Strasser 2007, 278.
[15] Aeneas’ use of astragali is discussed for the first time in modern cryptographic scholarship by Hunter and Handford in 1927 (Hunter & Handford 1927, 209).
[16] Olivetti 2015, 263.
[17] It is plausible that Aeneas Tacticus tried out the method before putting it into practice. In passage 31.18, namely, he discussed how to ‘write’ his own name by pulling a thread through the holes of the astragalus.
[18] Hunter and Handford 1927, lxxxii; Whitehead 1990, 187.
[19] Whitehead 1990, 87. If there is no actual writing involved in creating cryptographic messages, one speaks of a semagram (Chatton 2010, 43; Lunde 2012, 42).
[20] Diels 1914, 67.
[21] Welskopf 1974, 44.
Bibliography:
Barends, D. (1955). Lexicon Aeneium: a Lexicon and Index to Aeneas Tacticus' Military Manual "On the Defence of Fortified Positions". Assen: Van Gorcum.
Bauer, C. P. (2017). Unsolved! The History and Mystery of the World's Greatest Ciphers from Ancient Egypt to Online Secret Societies. New Jersey/ Woodstock: Princeton University Press.
Bengtson, H. (1962). Die griechische Polis bei Aeneas Tacticus. Historia: Zeitschrift für Alte Geschichte, 11 (4), 458-468.
Bliese, J. R. (1994). Rhetoric Goes to War: The Doctrine of Ancient and Medieval Military Manuals. Rhetoric Society Quarterly, 23 (3-4), 105-130.
Brown, T. S. (1981). Aeneas Tacticus, Herodotus and the Ionian Revolt. Historia: Zeitschrift für Alte Geschichte, 30 (4), 385-393.
Brownson, C. L. (1918). Xenophon: Hellenica (Volume I: Books 1-4; Loeb Classical Library 88). Cambridge (Massachusetts): Harvard University Press.
Burliga, B. (2008). Aeneas Tacticus between History and Sophistry: the Emergence of the Military Handbook. In J. Pigon, The Children of Herodotus. Greek and Roman Historiography and Related Genres. Newcastle: Cambridge Scholars Publishing, 92-101.
Chaniotis, A. (2013). Greeks under Siege: Challenges, Experiences, and Emotions. In: Campbell, B. & Tritle, L. (eds.), The Oxford Handbook of Warfare in the Classical World. Oxford/ New York/ Auckland/ Cape Town/ Dar es Salaam/ Hong Kong/ Karachi/ Kuala Lumpur/ Madrid/ Melbourne/ Mexico city/ Nairobi/ New Delhi/ Shanghai/ Taipei/ Toronto: Oxford University Press, 438-456.
Chatton, B. (2010). Using Poetry Across the Curriculum: Learning to Love Language. Santa Barbara: ABC-CLIO LLC.
Dain, A., & Bon, A. (1967). Énée le Tacticien : Poliorcétique. Paris : Les Belles Lettres.
David, E. (1986-I). Aeneas Tacticus, 11.7-10 and the Argive Revolution of 370 BC. Amercian Journal of Philology, 107 (3), 343-349.
Delebecque, E. (1957). Essai sur la Vie de Xénophon. Revue des Études Anciennes Année, 60 (3), 429-436.
Diels, H. (1914). Antike Technik. Sechs Vorträge. Leipzig and Berlin: Teubner.
Glotz, G., & Cohen, R. (1936). Histoire Grecque Tome III : La Grèce au IVe siècle; la Lutte pour L'Hégémonie (404-336). Paris: Les Presses universitaires de France.
Hanson, V. D. (2007). The Modern Historiography of Ancient Warfare. In: Sabin, P., Van Wees, H. & Whitby, M. (eds.), The Cambridge History of Greek and Roman Warfare (Volume 1: Greece, the Hellenistic World, and the Rise of Rome). Cambridge: Cambridge University Press, 3-21.
Hug, A. (1877). Aeneas von Stymphalos, ein Arkadischer Schriftsteller aus Klassischer Zeit: Gratulationsschrift der Universität Zürich an die Universität Tübingen zu deren vierhundertjähriger Stiftungsfeier vom VIII. - XI. August MDCCCLXXVII. Zürich: Zürcher & Furrer.
Hunt, A. S. (1929). A Greek Cryptogram. Proceedings of the British Academy 1929, 15, 127-134.
Hunter, L., & Handford, S. (1927). Aineiou Poliorkētika: Aeneas on Siegecraft. Oxford: Clarendon Press.
Jenkins, T. E. (1999). Intercepted Letters: Epistles and Their Readers in Ancient Literature. Cambridge (Massachusetts): Harvard University Press.
Kelly, T. (1985). The Spartan Scytale. In: Eadie, J. W. & Ober, J. (eds.), The Craft of the Ancient Historian: Essays in Honor of Chester G. Starr. Lanham: University Press of America, 141-169.
Lunde, P. (2012). The Secrets of Codes: Understanding the World of Hidden Messages. San Francisco: Weldon Owen.
Millett, P. (2013). Writers on War: Part 1 Greece: Winning Ways of Warfare. In: Campbell, B. & Tritle, L. (eds.), The Oxford Handbook of Warfare in the Classical World. Oxford/ New York/ Auckland/ Cape Town/ Dar es Salaam/ Hong Kong/ Karachi/ Kuala Lumpur/ Madrid/ Melbourne/ Mexico City/ Nairobi/ New Delhi/ Shanghai/ Taipei/ Toronto: Oxford University Press, 46-73.
Moore, R. (2013). Generalship: Leadership and Command. In: Campbell, B. & Tritle, L. (eds.), The Oxford Handbook of Warfare in the Classical World. Oxford/ New York/ Auckland/ Cape Town/ Dar es Salaam/ Hong Kong/ Karachi/ Kuala Lumpur/ Madrid/ Melbourne/ Mexico city/ Nairobi/ New Delhi/ Shanghai/ Taipei/ Toronto: Oxford University Press, 457-473.
O'Connor, B. (2018). Bletchley Park and the Pigeon Spies. Morrisville: Lulu.com (Online publishing company).
Oldfather, W. A. (1928). Introduction and Notes. In: Illinois Greek Club, Aeneas Tacticus, Asclepiodotus, Onasander. (Volume 156 Loeb Classical Library). Cambridge (Massachusetts): Harvard University Press.
Olivetti, L. (2015). Atlas of Imaging Anatomy. Springer / Cham / Heidelberg/ New York/ Dordrecht / London: Springer International Publishing Switzerland.
Pretzler, M. (2018). Aineias and History: The Purpose and Context of Historical Narrative on the Poliorketika. In: Pretzler, M. & Barley, N. (eds.), Brill’s Companion to Aineias Tacticus. Leiden/ Boston: Brill, 68 – 95.
Rawlings, L. (2007). The Ancient Greek at War. Manchester/ New York: Manchester University Press.
Sheldon, R. M. (1987). Tinker, Tailor, Caesar, Spy: Espionage in Ancient Rome. Ann Arbor: UMI Dissertation Information Service.
Shipley, D. G. J. (2018). Aineias Tacticus in His Intellectual Context. In: Pretzler M. & Barley. N. (eds), Brill’s Companion to Aineias Tacticus.Leiden/ Boston: Brill, 49–67.
Spence, I. G. (2010). The A to Z of Ancient Greek Warfare. Lanham/ Toronto/ Plymouth: The Scarecrow Press Incorporation.
Starr, C. G., 1957: Reviewed Work(s): Lexicon Aeneium. A Lexicon and Index to Aeneas Tacticus' Military Manual „On the Defence of Fortified Positions“ by D. Barends, Classical Philology, 52 (1), 68.
Strasser, G. F. (2007). The Rise of Cryptology in the European Renaissance. In: De Leeuw, K. & Bergstra, J. A. (eds.), The History of Information Security: A Comprehensive Handbook. Amsterdam/ Boston/ Heidelberg/ London/ New York/ Oxford/ Paris/ San Diego/ San Francisco/ Singapore/ Sydney/ Tokyo: Elsevier, 277-325.
Vela Tejada, J. (1991). Estudio sobre la Lengua de la Poliorcética de Eneas el Tactico. Zaragoza: Departamento de Ciencias de la Antigüedad de la Universida Zaragoza.
Vela Tejada, J. (2004). Warfare, History and Literature in the Archaic and Classical Periods: The Development of Greek Military Treatises. Historia: Zeitschrift für Alte Geschichte, 53 (2), 129-146.
Von Gutschmid, H. A. (1880). Review of Hug: A. Hug, Aeneas von Stymphalos: Ein Arkadischer Schriftsteller aus Klassischer Zeit. Literarsiches Zentralblatt 1880, 588-590.
Usher, S. (1970). Review of Aeneas Tacticus. Poliorcétique. Ed. A. Dain. Trans. A.-M. Bon. (Assn. G. Budé) Paris: ‘Les Belles Lettres’. 1967. Pp. lxv + 139. The Journal of Hellenic Studies, 90, 210-211.
Welskopf, E. A. (1974). Hellenische Poleis: Krise, Wandlung, Wirkung (Volume 4). Darmstadt: Wissenschaftliche Buchgesellschaf.
West, S. (1998). Archilochus' Message Stick. Classical Quarterly, 38, 42-48.
Whitehead, D. (1990). Aineias the Tactician: How to Survive Under Siege. Oxford: Clarendon Press.
Williams, T. H. (1904). The Authorship of the Greek Military Manual attributed to ‘Aeneas Tacticus.’ American Journal of Philology, 25 (4), 390‑405.
Winterling, A. (1991). Polisbegriff und Stasistheorie des Aeneas Tacticus. Zur Frage der Grenzen der Griechischen Polisgesellschaften im 4. Jahrhundert vor Christus. Historia: Zeitschrift für Alte Geschichte, 40 (2), 193-229.






